File: qq.rar
MD5: 97abe0065e045a8c99a7aac81fbdc821
Rising: Win32.Eirus.b
卡巴不报病毒
测试时间:2007-08-19
运行后病毒样本,自动删除病毒本身,自动复制副本到%SYSTEM%目录下
%SYSTEMroot%\svhostkeep.exe
%SYSTEMroot%\svhost.exe
x:\Documents and Settings\你的用户名\Local Settings\Temp\E_4\spec.fne
x:\Documents and Settings\你的用户名\Local Settings\Temp\E_4\eapi.fne
x:\Documents and Settings\你的用户名\Local Settings\Temp\E_4\iext2.fne及所创建的文件图二.
x:\Recycled\krnln.exe
X:\Program Files\QQ\QQ .exe<见下图>
删除桌面上QQ及QQ直播的,
X:\Documents and Settings\MIB\桌面\QQ
X:\Documents and Settings\MIB\桌面\QQlive5.0
并替换在桌面上的QQ快捷方式及QQ目录下的QQ文件.
x:\Documents and Settings\MIB\桌面\腾讯QQ.lnk
中止所有杀毒软件<俺的电脑使用的MACFEE,可惜没有中断掉,关闭了QQ医生,
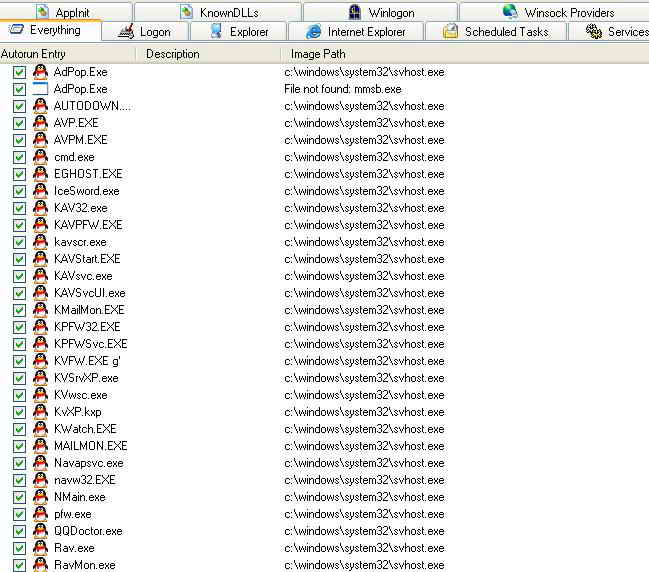
创建下列IFEO劫持项:如下图
"Debugger"="X:\windows\system32\svhost.exe
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AdPop.Exe]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AdPop.Exe ]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AUTODOWN.EXE]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVP.EXE ]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVPM.EXE ]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\cmd.exe]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\EGHOST.EXE]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\IceSword.exe]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KAV32.exe]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KAVPFW.EXE]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\kavscr.exe]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KAVStart.EXE]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KAVsvc.exe]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KAVSvcUI.exe]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KMailMon.EXE ]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KPFW32.EXE]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KPFWSvc.EXE]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KVFW.EXE g']
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KVSrvXP.exe]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KVwsc.exe]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KvXP.kxp]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KWatch.EXE]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\MAILMON.EXE]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Navapsvc.exe]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\navw32.EXE]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\NMain.exe]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\pfw.exe]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\QQDoctor.exe]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Rav.exe]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\RavMon.exe]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\RAVmonD.exe]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Ravtimer.exe]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\regedit.exe]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Rising.exe]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\RTHDCPL.EXE]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\srtask.exe]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\TBSCAN.EXE]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\TCA.EXE]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\THGUARD.EXE]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\TrojanHunter.exe]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\WEBSCANX.EXE]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\wmiprvse.exe]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\WoptiProcess.exe]
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\修复工具.exe]
附SRENG(该工具可到down.45its.com下载)日志:
[HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Winlogon]
[(Verified)Microsoft Corporation]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AdPop.Exe]
[]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AdPop.Exe ]
[N/A]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AUTODOWN.EXE]
[]
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVP.EXE ]
[]
HOSTS 文件
127.0.0.1 www.360safe.com
127.0.0.1 360safe.com
127.0.0.1 www.skycn.com/soft/3252.html
127.0.0.1 skycn.com/soft/3252.html
127.0.0.1 Xww.skycn.com/soft/24158.html
127.0.0.1 skycn.com/soft/24158.html
127.0.0.1 mmsk.cn
127.0.0.1 wXw.mmsk.cn
127.0.0.1 wXw.luosoft.com/index1.htm
127.0.0.1 wXw.luosoft.com/index2.htm
127.0.0.1 wXw.luosoft.com/index3.htm
127.0.0.1 luosoft.com/index3.htm
127.0.0.1 wXw.luosoft.com
127.0.0.1 luosoft.com
127.0.0.1 safe.qq.com/product
127.0.0.1 safe.qq.com
127.0.0.1 wXw.safe.qq.com/product
127.0.0.1 wXw.safe.qq.com
127.0.0.1 wXw.onlinedown.net/soft/37369.htm
解决方法:
1.下载把IceSword.exe(该软件可到down.45its.com下载)更改软件名为:ceSword.exe,双击运行后.
文件---设置---禁止进线性创建,结束病毒进程:svhost.exe
2.直接使用lceSword.exe删除病毒文件
%SYSTEMroot%\svhostkeep.exe
%SYSTEMroot%\svhost.exe
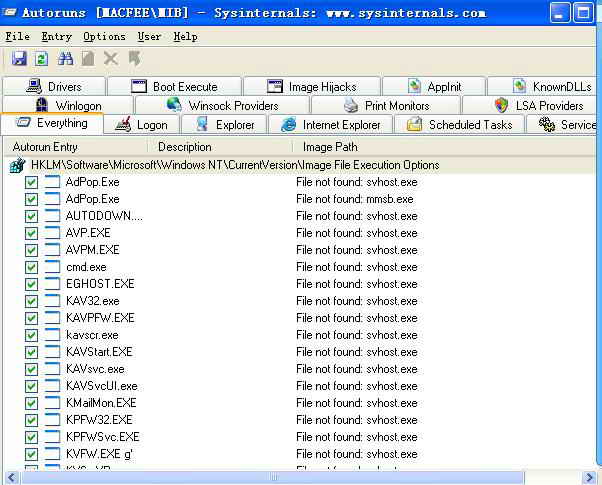
嘻嘻!在这里没有把autoruns劫持,取消禁止进线性创建后,直接运行autoruns<见下图>,一步一步删除也行,
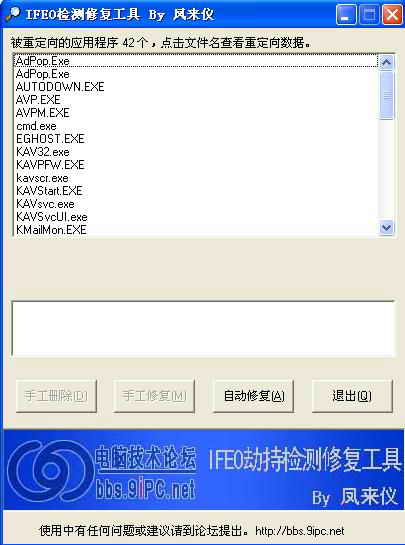
想偷懒可以使用其它工具来修复.在这里推荐举使用大哥的.IFEOS检测修复工具(该软件可到down.45its.com下载).见下图
3.运行SREng2(该软件可到down.45its.com下载),使用“启动项目”--注册表--选择要修改的项
,点“编辑”在“值”里删除C:\Recycled\krnln.exe,svhost.exe>
4.重置HOSTS文件.
5.运行SREng2,使用:系统修复--文件关联--全选--修复
6.卸载掉QQ.同时删除QQ文件夹.重新安装一次.
7.x:\Documents and Settings\你的用户名\Local Settings\Temp\E_4\删除文件夹.